all,
I have subdirs on one of my sites where I keep sensitive info for downloading purposes (for instance, solutions for clients) and the other day I saw an authorized page render come through. these subdirs are currently PW protected using a godaddy cPanel tool, but everyone knows that hosting companies know nothing about anything. they are pushing the concept of a firewall to get rid of this activity, and they say it will filter IPs so certain countries or regions can be blocked out. and of course, it is a paid-for service. but I know good and well I can do it for free using other methods. heck, I could write a simple query and only allow IP addresses from the client’s country and city if I wanted to. Just not render anything to the page unless it is them.
I got this knowledge from @astonecipher a long time ago: https://www.devdungeon.com/content/http-basic-authentication-php#toc-2
either that, or this one: https://cwiki.apache.org/confluence/display/HTTPD/PasswordBasicAuth
my question is…will this keep unauthorized people out for sure? and how much risk is there? obviously I can’t have proprietary info in a subdir, available for client downloading in the form of a ZIP if bots or other large companies running automation specifically for the purposes of spying in a desperate attempt to find out what others are up to and copy them to keep their profits going, if nothing works.
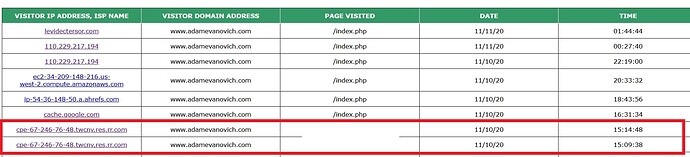
Can someone shed some light on this? I can do a few workarounds, as I’ve done it for decades, but that takes too much time. thanks. see image below and subsequent links for the occurence that got around Godaddy’s canned software security:
TIME WARNER CABLE IP ADDRESSES that accessed the page:
https://www.ip-tracker.org/locator/ip-lookup.php?ip=67.246.76.48
https://www.ip-tracker.org/locator/ip-lookup.php?ip=cpe-24-59-255-122.twcny.res.rr.com