Hello,
I got this message from google
There was a folder named “07092021” in a folder on the remote server
Contents:
What precautions should be taken for such things?
Thank you

Hello,
I got this message from google
There was a folder named “07092021” in a folder on the remote server
Contents:

What precautions should be taken for such things?
Thank you
What do you mean? You can not see PHP code on any site. Unless the site is set up to let you view code on their site. What are you worried about? Normally you can not see contents of folders on servers unless the owner want you to. If the folder is named with a date, most likely it is some sort of post, but, it is unusual to be able to see the files inside it.
What do you mean by social engineering content?
?? No clue what your saying?
Did you create this folder? Or are you saying you DID NOT create this… and it was created by an outside source/user? (if so… you have security issues… big time)
If you did create this… and you are seeing a display of the folder/directory contents… then you need to turn that off.
Please elaborate more.
Someone else (hacked) created a file on my website
Email was sent to me by Google
They said, “Because your website contains content that deceives users, we have lowered its rank and set it as a dangerous site”
When I connected to the server with FTP and looked at the specified folder, there was this folder “07092021” and I downloaded it to my computer to look at it and deleted it from the server.
I sent a message to Google saying that the problem has been fixed. Google sent me the message confirming it was fixed. My website is now normal no problems.
If you want to view the files, you can download them here.
I looked and did not understand anything
Download File Here
Well, we don’t want to look at some third party’s hacker files.
You must have a problem with your folder permissions. Normally, you set up the folders to only be accessible from FTP ( with username and passwords ) or from internal PHP files only. You set the permissions to not allow others to randomly install things on your server.
To fix this you use the CHMOD command or use your FTP application. There are basically three settings for each user’s access. Read, Write, Edit. I think… And, you set these on every folder in your server. In most FTP applications, you can set a default when you create a folder. If you need more info on this, Google website folder permissions and you will find tons of info on how to do it. Or ask here…
How is this done?
I did not set any permissions. Default permission settings are being used.
I’m trying to learn how to make these
The permissions of the folder where foreign people leave files are as in the picture.
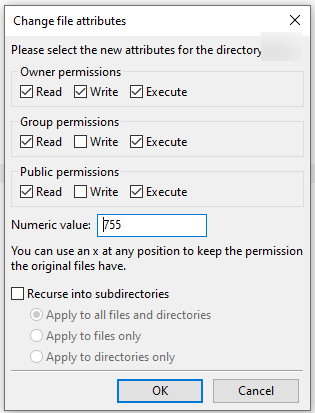
Any problems with permissions?
I run the php files inside this folder with ajax. Could this be the problem?
edit:
I checked in detail today, there was a “07092021” folder inside the css folder. There was also a php file in the home directory. I deleted all
Well, there are permissions on both folders and on files. Normally, 755 is used for folders.
While developing, it is often set to 775, but, 755 will work for PHP developing. So, yes, 755 is good.
For individual files, you set them to 644. That is a bit tedious to do as you need to set every file.
But, it protects your files from others. Or 640 as that is more secure.
For updating things such as pictures, you should always let your PHP script do that. Never give others permission to use FTP or other file upload protocols. With your PHP code controlling uploads, you can make sure it is only handled from members that are verified.
Under all of this, there is the user security which almost nobody seems to use in their servers. Bascially, Apache sets a master user for the server. This user is most often set to " www-data " and is set up for basic security. You can alter that if you are very careful and create a different owner. It’s a little complicated. I would just start with the 755 and 640 settings. Those will stop others from creating files
If you want to read up on this, here is a link that covers just about everything. You have to read all the replies as they contain issues that you can study up on. It also covers changing the root owner of the site. I would not do that unless you are 100% sure you understand all of that section. Permissions
When you upload files to the remote server, you do not use the default permissions, do you change the permissions again?
I’m looking at the last modification dates of the web home directory every day until I set the permissions
You normally do not worry about files uploaded by members, just yourself. If you set the folder’s permissions correctly, you should be all set. Just do not let anyone but the owner upload files to the folders except the public ones such as profile pictures.
No file upload feature
Only the manager and the dealer uploads a profile picture and company logo to himself in the management panel and sees them himself, and it is not open to everyone.
A folder permission for the PDF file is 777 only when the quote is created. and inside this folder there is “.htaccess” and permission setting is “deny from all”.
Already admin panel directory encrypted
Conclusion: I need to be very careful for Directory and File permissions, I shouldn’t ignore it.
Thank you
I would also suggest you HEAVILY check the file types and block/allow specific file types
things like .txt, .pdf. .jpg…etc no .exe’s… or .php scripts…etc
Well, yes, the permissions are important for security. And, yes, you should not allow ALL file types uploaded as Whispers suggested. Normally, for images, you limit them to the base types of images or force the users, or managers in this case, to just use standard JPG’s… But, for security, make sure you can only upload files from the OWNER. This means that only your webpages can upload images and you will of course only allow logged in managers to be able to do that. Random visitors would only be able to view other areas and not upload images…
I am using “I am not a Robot” input fields for Guest Visitors.
Guest visitors can only upload images for the Company Logo and I check with php if there is an image.
Other operations continue in the administration panel
What I’m wondering is:
Are the created folder and files created using my php codes?
Created? No.
Uploaded using exploits in your scripts/code… more likely.
Thank you
I need to review the codes as soon as possible
For google to have detected the contents in this folder, it must have been linked to by something in your main files, so it’s likely that your main web page file(s) have been altered and need to be compared with a known good backup.
The following are the ways that someone can get their server-side code onto your server or to be executed on your server, which then can do anything, such as deposit folders/files, edit existing files, … -
Seems like it’s possible this is being done via code injection. You should research and understand what and how that is done. Then review all of your files for where that may happen at. Make sure you sanitize input from users. Research how to do that as well. Finally you should learn about XSS and sql injection though they’re less likely to be the reason.
This just triggered a memory of an exploit. A commonly used Apache (and perhaps other web server) configuration setting to detect php files would invoke php if the file name contained “.php” anywhere in the name, so somename.php.jpg would end up invoking php. Next, if the file starts with valid image data, but has php code after it, any sort of image test you do on the file will tell you that it is an image, but if it is requested and invokes the php language engine, the starting image data will simply be output to the browser, then the php code in the file will be executed on the server.
I’m using a Linux VPS,
I reported this to the server and gave the link to this topic.
Actually hacked before
hacked on joomla installed site
hacked on webtrees installed site
and finally now the site with the code I wrote has been hacked
You are right, there may be a problem with the server.